The rise of the Internet is undeniable, and unrestricted access from multifarious smart gadgets with more rapid 4G connectivity means that consumers’ potential usages of these devices in terms of the tasks they can accomplish online at any time an at any place are growing fast. In this milieu, the subject of online retail and its correlation with personal communication (either face-to-face or via phone) is being fervently discussed in all sectors.
And so it goes for insurance as well. For the past thirty years, personal connections have been dominated by the contact centre, and while not many can question that the Internet has greatly aided in generating quotes, the accepted rule is that phone calls and in-the-flesh visits are still a vital part of the sales cycle and a major force in enhancing conversion rates. While many situations may call for the application of the personal appearance, it is nevertheless the case that a rising share of everyday insurance tasks can be accomplished without it – in so far as the consumer agrees to it.
Mounting demand for self-service
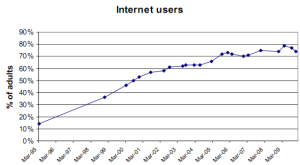
Instances of these cases include online banking or even grocery check-outs show a significant – and increasing – percentage of consumers would rather ‘operate the system’ themselves, especially if it leads to avoiding queues and being able to finish such chores at their most convenient time.
As it applies now to the insurance sector, Junction recently revealed that one million BGL customers now choose to handle their own policies online. In the same manner, Ageas Insurance Solutions’ biggest motor brand, Auto Direct, moved to a self-service website earlier this year and saw 97% of its clients immediately opt for electronic documentation and messaging over paper.
It is certainly counter-intuitive to bypass this need for self-service, especially in insurance, where the advantage of the aggregator brands has produced a largely price-sensitive market.
Source: Hass and Associates